What is Phishing? How To Protect Your Data From Cybercriminals, Personal Examples

Phishing is a form of social engineering where attackers try to trick you into revealing sensitive information.
They often use emails, text messages, or even fake websites that appear legitimate.
These messages typically create a sense of urgency or fear, pressuring you to act quickly without thinking critically.
The term "phishing" itself is a play on the word "fishing,"
Referencing how attackers cast a lure (the fake message) to catch sensitive information. (from the target)
I recently booked a trip for my vacation.
Two days after the booking I got an e-mail.
The Hotel where I booked wrote me a message...
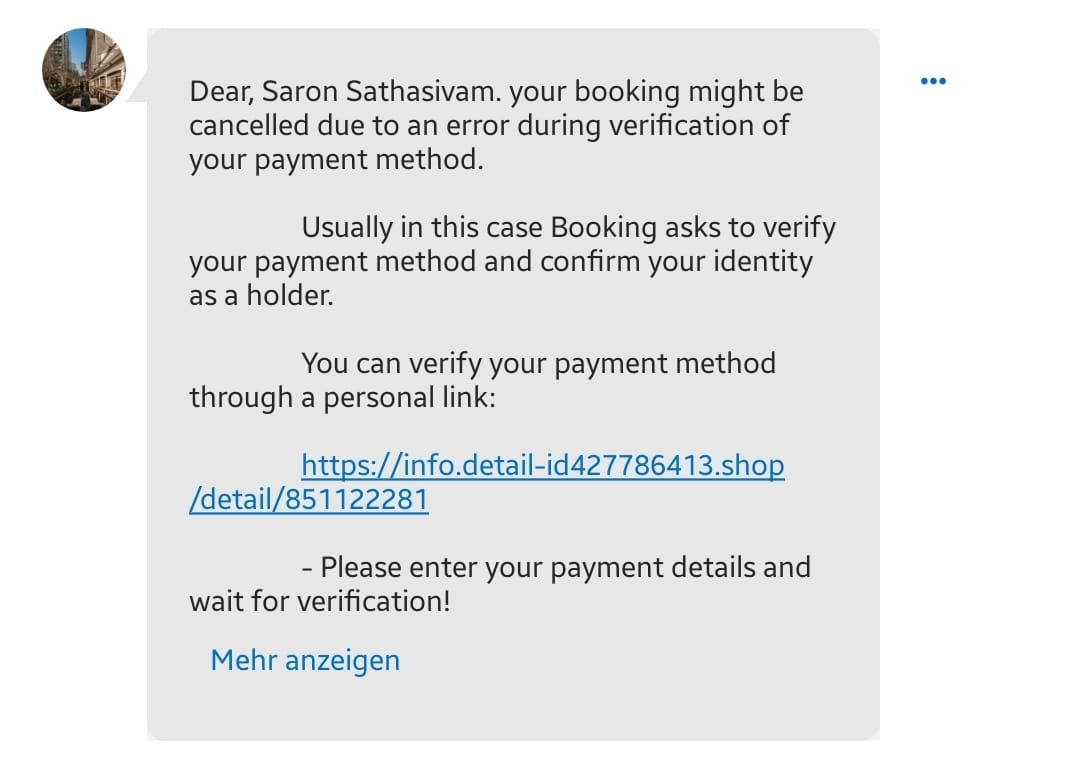
My alarm bells rang as soon as I saw:
- The weird formatting of the message
- The urgent call to action (in this case verifying my payment)
- The Link (started with "info.detail....")
This is a typical case of phishing or smishing (SMS fraud).
Turns out cybercriminals had gotten access to the booking system of the hotel. I notified them to get it fixed ASAP.
I will be using my hotspot to access the internet. Not the one from the hotel.
As a security precaution.
↓
What are the goals of phishing?
Phishers have various malicious goals, including:
- Stealing personal information (PII): Cybercriminals can use your stolen data to access your bank accounts, credit cards, or other financial resources.
- Gaining access to your accounts: With your login credentials, they can hijack your email, social media accounts, or other personal accounts.
- Installing malware: Clicking malicious links in phishing messages can infect your device with malware, such as ransomware, which can lock your files and demand payment for their release.
- Identity theft: Criminals use your personal information to open new credit cards, rack up debt, and damage your credit score.
How to recognize phishing attempts:
- Be cautious of unsolicited messages: Phishing messages often come from unknown senders or impersonate legitimate organizations.
- Check the sender's address: Don't just rely on the displayed name; scrutinize the actual email address for inconsistencies.
- Beware of urgency and threats: Phishing messages often pressure you to act quickly due to a "critical issue" or threaten consequences if you don't comply.
- Suspicious links and attachments: Don't click on links or open attachments from unknown senders or messages that seem suspicious.
- Grammatical errors and inconsistencies: Phishing messages often contain typos, grammatical errors, or formatting issues that can raise red flags.
How to stay protected from phishing:
Verify the sender:
- Don't rely solely on the sender's name or email address. Look closely at the full address and check for any misspellings or inconsistencies.
- If you're unsure, contact the supposed sender directly through a trusted channel like their official website or phone number.
Inspect the link before clicking:
- Hover your mouse over the link without clicking it. Check if the displayed address matches the actual destination URL (the text that shows up when you hover).
- Avoid clicking on shortened links as they can mask malicious websites.
Be wary of urgency and threats:
- Scammers often create a sense of urgency or fear to pressure you into clicking on a link or providing information. Don't rush into any action, and take time to think critically about the message.
Protect your personal information:
- Never share your passwords, account details, or social security numbers with anyone through emails, texts, or calls. Legitimate organizations won't ask for this information through these channels.
Use strong and unique passwords:
- Avoid using the same password for multiple accounts.
- Consider using a password manager to create and store strong, unique passwords for each of your accounts.
Enable two-factor authentication (2FA):
- This adds an extra layer of security to your accounts, requiring a code from your phone or another device besides your password when logging in.
Stay informed:
- Keep yourself updated on the latest phishing scams and tactics. You can find information from trusted sources like cybersecurity organizations or government agencies.
Report phishing attempts:
- If you receive a suspicious email, report it to the sender's legitimate email provider and your email provider.
- Don't trust any message demanding immediate action or claiming your account is at risk.
Remember:
If you suspect a phishing attempt.
Do not respond to the message, click on any links, or open any attachments.
Report the message to the relevant platform (email provider, social media platform, etc.) and delete it immediately.
What to do in case of emergency
1. Secure your accounts:
- Change Passwords: Change the passwords for all accounts you might have entered information on the phishing site. Use strong, unique passwords for each account, and consider using a password manager to help you keep track of them.
- Enable Multi-Factor Authentication (MFA): If available, enable multi-factor authentication (MFA) on all your sensitive accounts. This adds an extra layer of security, making it harder for unauthorized access even if your password is compromised.
- Freeze your bank accounts: Call up your bank and ask them to freeze your bank accounts temporarily.
2. Monitor your accounts:
- Review Statements: Closely monitor your bank statements and credit card reports for any suspicious activity. Report any unauthorized transactions immediately to your financial institution.
- Enable Fraud Alerts: Consider setting up fraud alerts with your financial institutions to be notified of any suspicious activity on your accounts.
3. Consider additional steps:
- Run a scan: Depending on the situation, running a thorough malware scan with your security software or consulting a cybersecurity professional might be necessary to ensure your device is not compromised.
- Report the incident: Report the phishing attempt to the relevant authorities. This helps track and potentially take down phishing campaigns, preventing others from falling victim.
Sources for reporting incidents:
Switzerland:
https://www.report.ncsc.admin.ch/en/
Germany:

UK:

US:



